Key Security Features in Windows 7
- Windows 7 Action Center
- Centralized reporting center for users to keep track of issues and messages about their local computer
- Categorized by severity to get action items and events
- Color-coding for severity alerts
- Encrypting File System (EFS)
- About encrypting information while it’s at rest (theft of laptops)
- A built-in encryption tool for Windows files
- Windows BitLocker and BitLocker To Go
- Introduced with Windows Vista, protects data on a computer exposed to unauthorized physical access
- Available in Enterprise and Ultimate editions of Windows 7
- Locks the operating system and removable drives such as USB drives and portable hard drives
- Renders data inaccessible when drives are decommissioned or recycled
- Windows AppLocker
- Restricts the types of applications you can run and install
- Allows administrators to specify the apps that are allowed
- User Account Control
- Checks for permissions when performing necessary daily tasks
- Windows Firewall with Advanced Security
- Restricts unsolicited traffic coming and going
- Security rules to provide protection from malware
- Windows Defender
- Prevents and removes all forms of malware
Action Center
- Action Center is a central location for viewing messages about your system
- Action Center is the starting point for diagnosing and solving issues with your system
- Action Center replaces Windows Security Center in Windows 7
- Action Center includes access to four essential security features
- Select items you want checked for user alerts
- Action Center notifies you with a message in the notification area of the taskbar
- Color-coded to indicate the severity of the message
- Two categories of messages that require your attention are found in the new Action Center
- Normal
- Important
Change Action Center Settings
- Start/Control Panel
- Click System and Security
- Click Action Center
- Under Virus protection (Important), click the Turn off messages about virus protection link
Change User Control Settings
- In the left pane of Action Center, click Change User Account Control settings
- Change when to be notified about changes to your computer by using the sliding scale
Securing a Client Using Local Security Policy
What is Group Policy?
Group Policy allows IT admins to automate and manage multiple users and computers using a centralized model. You can define the user's work environment once and rely on the system to enforce the defined policies.
Use Group Policy to:
- Apply standard configurations
- Deploy software
- Enforce security settings
- Enforce a consistent desktop environment
Local Group Policy is always in effect for local and domain users, and local computer settings.
How are Group Policy Objects Applied?
Computer settings are applied at boot and at regular intervals, while user settings are applied at logon and at regular intervals. The default refresh interval is every 90 minutes.
Group Policy Processing Order:
- Local computer GPOs gets applied first
- Site-level GPOs
- Domain GPOs
- Organizational Unit (OU) GPOs gets applied last
If you have multiple policies at one level, the last one applied has the highest precedence, though you can change this behavior as needed.
How Mulitple Local Group Policies Work (MLGPO)
- The local group policy contains the user and computer settings.
- Administrator and non-administrator local group policy.
- Specific user local group policy is applied last. (Highest precedence, "Last Writer Wins" method)
Demo – Creating Multiple Local Group Policies
- Start/ Type mmc to bring up the mmc console
- File/Add or Remove Snap-ins
- Select Group Policy Object Editor
- In the Select Group Policy Object dialog box, click Finish (This is for the Local Computer Policy)
- Select Group Policy Object Editor
- Click Browse button
- Click the Users tab
- Highlight Administrators
- Click OK (This is for Local Computer\Administrators)
- Select Group Policy Object Editor
- Click Browse button
- Click the Users tab
- Highlight Non-Administrators
- Click OK (This is for Local Computer\Non-Administrators)
- Click OK
- Click File/Save As an MMC to your desktop if you want or pin to your taskbar so it is available for reuse
Demo - Create a Local Security Policy
- Click on the MMC you saved above in your taskbar
- Highlight Local Computer Policy
- Under Windows Settings, highlight Security Settings
- Click on Account Policies
- Click on Account Lockout Policy
- Highlight Account lockout threshold
- Double-click Account lockout threshold
- Click the drop-down box to the number 2 (this means you will be locked out after two invalid logon attempts)
- Click OK
- A dialog box pops-up that has Account lockout duration and Reset account lockout counter after 30 minutes(these are suggested values)
- Click OK
- Start/All Programs/Accessories
- Right-click on Command Prompt and Run as administrator
- User Account Control dialog box opens
- Click Yes
- Command prompt displays/type gpupdate /force
- ‘’User Policy update has completed successfully.’’ message displays
- Close the command prompt
- Save the MMC
What is EFS?
EFS is built-into NTFS and designed to enable transparent file encryption and decryption by using advanced, standard cryptographic algorithms.
If a user moves or copies an encrypted file to a non-NTFS file system, the file will no longer be encrypted.
If a user moves or copies an encrypted file to a non-NTFS file system, the file will no longer be encrypted.
Utilizes asymmetric and symmetric key encryption.
Symmetric means the key you use to encrypt the data is the same one you use to decrypt.
Asymmetric means the key used to encrypt the data and decrypt the data, has to be different. A public and private key is used to facilitate this process. The key can be self-generated or issued from an internal or third party CA (Certificate Authority) and designed to be protected by the user’s passwords. Using a CA allows the key to be managed centrally, including backups.
If a CA is not available, users can generate a key pair and the keys have a lifespan of one hundred years. There is no centralized management for self-generated keys and users are responsible for managing their own keys. Users must manually backup self-generated EFS certificates and keys. If the user forgets the password and has to have the key reset, they will not be able to get into their files any longer.
If a CA is not available, users can generate a key pair and the keys have a lifespan of one hundred years. There is no centralized management for self-generated keys and users are responsible for managing their own keys. Users must manually backup self-generated EFS certificates and keys. If the user forgets the password and has to have the key reset, they will not be able to get into their files any longer.
However, if you set the key up through Active Directory, there is a Recovery Agent the administrators are usually a member of and can decrypt the files.
EFS encryption occurs at the file-system level. When a folder is marked for encryption, every file in the folder will be encrypted.
EFS allows files to be shared with other valid EFS user certificates. You must first encrypt the file and save it before adding additional users.
If a user attempts to open an encrypted file and does not have the key, they will received an "Access denied" error message.
This type of encryption system is referred to as a Public Key Infrastructure (PKI).
If an encrypted file is saved to or opened from a folder on a remote server, the files do not remain encrypted during transport. The file is decrypted and traverses the network in plaintext. The file is encrypted locally if it is saved to a folder on the local drive and the folder is marked for encryption. EFS-encrypted files can remain encrypted while traversing the network if the files are saved to a Web folder using WebDAV.
Back up Encrypting File System (EFS) certificate
New EFS Features in Windows 7
EFS encryption occurs at the file-system level. When a folder is marked for encryption, every file in the folder will be encrypted.
EFS allows files to be shared with other valid EFS user certificates. You must first encrypt the file and save it before adding additional users.
If a user attempts to open an encrypted file and does not have the key, they will received an "Access denied" error message.
This type of encryption system is referred to as a Public Key Infrastructure (PKI).
If an encrypted file is saved to or opened from a folder on a remote server, the files do not remain encrypted during transport. The file is decrypted and traverses the network in plaintext. The file is encrypted locally if it is saved to a folder on the local drive and the folder is marked for encryption. EFS-encrypted files can remain encrypted while traversing the network if the files are saved to a Web folder using WebDAV.
Back up Encrypting File System (EFS) certificate
New EFS Features in Windows 7
- Support for Storing Private Keys on Smart Cards
- Encrypting File System Rekeying Wizard
- New Group Policy Settings for EFS
- Encryption of the System Page File
- Per-User Encryption of Offline Files
Demo – Encrypting and Decrypting Files and Folders by Using EFS
- Click on your C: drive
- Right-click and click New Folder
- Name it ENCRYPT
- Click ENCRYPT
- Click New Text Document
- Name the file ProtectMe
- Double-click on the file and write something
- Save it
- Go back to the root C:
- Right-click/Properties
- Click on Advanced in the General tab
- Click Encrypt contents to secure data
- Click Apply
- Confirm Attribute Changes dialog box appears asking “Do you want to apply this change to this folder only, or do you want to apply it to all subfolders and files as well?”
- Click OK
- Click OK (The file name is green (encryption))
To decrypt
- Go to the ENCRYPT folder on the C: drive
- Right-click ENCRYPT
- Select Properties
- Click Advanced
- Turn off the Encryption
- Click Apply
- Click OK
- Click OK
What is BitLocker?
Introduced in Windows Vista. Available on the Enterprise and Ultimate editions of Windows 7.
Uses a set of system integrity verifiers. TMP compares a hash of the OS configuration with an earlier snapshot. If anyone changes anything about your encrypted information, the hash changes, and the system locks the drive and puts you into recovery mode. It keeps the operating system safe, as well as your data. BitLocker ensures the integrity of your data, even with the theft of your hard drive.
BitLocker requires one of two hardware components in order to operate effectively:
- Your computer must be running TPM (Trusted Platform Module), version 1.2 or later. TPM is a microchip used to store cryptographic information like encryption keys. The TPM specialized chip installed on the motherboard of many newer computers by the manufacturers, but is not always activated. You might have to enable TPM by entering the BIOS setup, typically in the Advanced section. TPM works with BitLocker to help protect user data and ensure the computer has not been tampered with while offline.
- You need to have a removable USB memory device with the key to unlock it. You can also employ an the option to use a pin code for multifactor authentication.
The BIOS has to support a boot up from the TPM or USB memory device.
You have to have enough hard drive space for BitLocker to create the partitions.
Drives are automatically prepared for use in Windows 7. No need to manually create separate partitions before you enable BitLocker. The system partition created by Windows 7 does not have a drive letter so that data cannot be written to it.
Drives are automatically prepared for use in Windows 7. No need to manually create separate partitions before you enable BitLocker. The system partition created by Windows 7 does not have a drive letter so that data cannot be written to it.
BitLocker Modes
- TPM mode
- BitLocker will lock the normal boot process until the user enters the appropriate pin or inserts a USB drive containing the encryption key
- Non-TPM mode
- Uses Group Policy to allow BitLocker to work without TPM
- The BitLocker startup key has to be on a USB drive or smart card
- Provides very limited authentication options
- Provides encryption, but not the added security of locking keys with the TPM
Enable BitLocker without a TPM from Group Policy Settings for BitLocker
- Start/ type: gpedit.mc in the Search field and press Enter
- Accept the UAC prompt, if you receive one
- In the Local Group Policy Editor, Computer Configuration/Administrative Templates/Windows Components/BitLocker Drive Encryption/Operating System Drives
- Double-click Require additional authentication at startup
- Enable this policy and select the Allow BitLocker without a compatible TPM option
- Click OK
- Close the Local Group Policy Editor
- Click Start/ type: gpupdate /force in the Search field and press Enter to force Group Policy to apply immediately
note: If your computer comes with a TPM, you can enable BitLocker directly without accessing Group Policy.
- Start/Control Panel/System and Security/BitLocker Drive Encryption.
- The Help protect your files and folders by encrypting your drives dialog box displays. You can also access the utility by typing bitlocker into the Start menu Search field and selecting BitLocker Drive Encryption from the Programs list.
- Beside the drive you want to encrypt, click the Turn On BitLocker link. You can also right-click the desired drive in an Explorer window and choose Turn On BitLocker
- If you receive a UAC prompt, click Yes to proceed
- The BitLocker Drive Encryption window displays, and after a few seconds, this window displays the Set BitLocker startup preferences page.
- Select from these options;
- Use BitLocker without additional keys (Uses the TPM Only mode for validation, enabling the computer to startup without user interaction. If any hardware component has changed, BitLocker will lockup.
- Require a PIN at every startup (Uses the TPM and PIN option and requires the user to enter a PIN at startup)
- If you selected the Require a PIN at every startup, enter the pin and confirm and click Save.
- Require a Startup key at every startup (Creates a startup key and writes it to a USB flash drive. If your computer does not have a TPM, this is the only option available)
- If you selected the Require a Startup key at every startup, when prompted you will need to insert the USB drive and click Save.
- How do you want to store your recovery key? page has three options:
- Save the recovery key to a USB flash drive
- A dialog box displays. Insert the USB device, select it in the list, and click Save
- Save the recovery key to a file
- Print the recovery key
- Make sure you save the printed document in a secure location
- Are you ready to encrypt the drive? dialog box displays. Make sure the Run BitLocker system check box is selected and click Continue to encrypt your partition.
- Click Restart now to restart your computer and start the encryption. Windows 7 displays an icon in the notification area. You can use your computer while the encryption process is happening. Track the encryption progress by hovering your mouse over the icon. It will take an hour or longer and you are informed once the encryption is complete.
- Click Close
- Turn Off BitLocker
- Allows you to remove BitLocker protection
- Select Turn Off BitLocker and in the BitLocker Drive Encryption dialog box that appears, select Decrypt Drive
- The process begins immediately and your volume is decrypted and encryption keys are discarded
- You can monitor the process in the notification area on an icon
- Suspend Protection
- Allows you to disable BitLocker temporarily
- After selecting this option, the option changes to Resume Protection. Click to reenable BitLocker.
- Manage BitLocker
- Allows you to save or print the recovery key again or to duplicate the startup key
Three methods to start BitLocker
- System and Settings in Control Panel
- Right-click the volume to be encrypted in Windows
- Use the command-line tool manage-bde.wsf
BitLocker To Go
Encrypt a drive by right-clicking a portable device and turning on BitLocker.
Creates a virtual volume on the USB drive that is encrypted. The encryption key stored in the flash drive.
Creates a virtual volume on the USB drive that is encrypted. The encryption key stored in the flash drive.
When you do this, you have to choose some of the settings on how to unlock it:
- Recover password
- Smart card
- Auto unlock the device based on the information in Active Directory
- Start/Control Panel/System and Security/BitLocker Drive Encryption
- The Help protect your files and folders by encrypting your drives dialog box displays
- Insert the USB drive and click Turn On BitLocker beside the drive icon
- The Choose how you want to unlock this drive dialog box displays
- Use a password to unlock the drive
- Type and confirm a strong password
- Use my smart card to unlock the drive
- Insert the smart card in your reader
- Click Next
- On the Encrypt the Drive page, select Start Encrypting
- Do not disconnect your drive until encryption is completed
Group Policy settings to help you manage BitLocker:
- Computer Configuration/Administrative Templates/Windows Components/BitLocker Drive Encryption
- Fixed Data Drives (internal hard drive partitions containing data but not operating system files)
- Configure use of smart cards on fixed data drives
- Deny write access to fixed drives not protected by BitLocker
- Allow access to BitLocker-protected fixed data drives from earlier versions of Windows
- Specifies if drives formatted with FAT or FAT32 file systems can be unlocked and viewed on earlier Windows computers (back to Windows XP SP2).
- Configure use of passwords for fixed data drives
- Choose how BitLocker-protected fixed drives can be recovered
- Similar to the operating system drive policy
- Operating System Drives
- Require additional authentication at startup
- Enables use of BitLocker on a computer without TPM
- Specify whether BitLocker requires additional authentication, a startup key and/or PIN
- Require additional authentication at startup (Windows Server 2008 and Windows Vista)
- Similar settings except both a startup key and PIN cannot be used
- Allow enhanced PINs for startup
- Allows the use of a PIN containing additional characters, upper and lowercase letters, symbols, numerals, and spaces
- Configure minimum PIN length for startup
- 4 to 20 digits
- Choose how BitLocker-protected operating system drives can be recovered
- Enables the use of a data recovery agent
- Configure TPM platform validation profile
- Specify how the TPM security hardware secures BitLocker encryption key
- Removable Data Drives
- Same policies as fixed drives
Recovering BitLocker Encrypted Drives
If BitLocker detects a security risk, BitLocker enters recovery mode and keeps the system drive locked. The user must enter the correct Recovery Password to continue. The Recovery password can be stored in Active Directory and is a 48-digit password divided into eight groups you have to enter in recovery mode. During recovery, use the function keys to type the password into the BitLocker recovery console.
App Restrictions
AppLocker
Designed to protect our systems from running unwanted applications and allows IT professionals to specify what is allowed to run on our desktops. AppLocker does not prevent you from installing the application. That is UAC. AppLocker provides the ability to create rules to control how users can run an application and prevents unlicensed code from running.
AppLocker applies to standard users. AppLocker rules do not apply to administrators.
- Provides the ability to control how users run all types of applications, including executables, scripts, Windows Installer files, and DLL files
- Offers new application lockdown policies
- Includes support for legacy Software Restriction Policy (SRP) rules
- Does not support backward compatibility for the new AppLocker rules on Windows XP and Windows Vista
AppLocker Rules
- Default rules
- Without default rules, critical system files might not run
- Once rules are created, only apps affected by the rules are allowed to run
- Custom rules
- You can manually create a rule for a given executable
- You can automatically generate rules for a specific folder of executables
Demo – Configure AppLocker
- Type: Start/gpedit.msc to bring up Local Group Policy Editor
- Under Computer Configuration, expand Windows Settings
- Expand Security Settings
- Expand Application Control Policies
- Double-Click on AppLocker
- Click on Executable Rules
- Right-click and select Create New Rule.
- Click Next
- When the Permissions dialog box displays, click on Deny, then click Select.
- In the Select User or Group dialog box, in the Enter the object names to select box, type: Contoso\Tech (example), click Check Names, and click OK.
- Click Next
- On the Conditions screen, select Path, then click Next
- Click Browse Files..., then click Computer.
- Double-click Local Disk (C:).
- Double-click Program Files.
- Browse for Windows Media Player and click Open
- Choose wmplayer.exe and click Next
- Click Next
- Click Next.
- Click Create. Click Yes if prompted to create default rules.
- In the Local Group Policy Editor, expand Computer Configuration, expand Windows Settings, expand Security Settings.
- Expand Application Control Policies
- Click on AppLocker, then select Properties and right-click
- O the Enforcement tab, under Executable rules, click the Configured checkbox and select Enforce rules
- Click OK
- Click Start/ Search/type: cmd
- Press Enter
- In the Command prompt window, type gpupdate /force and press Enter.
- Click Start, right-click Computer and click Manage
- Expand Services and Applications, and select Services
- Right-click Application Identity service in the main window, and click Properties
- Set the Startup type to Automatic, and click Start
- Click OK when the service starts
- Log off
- Designed to help control unknown code – malicious or not
- AppLocker in Windows 7 replaces SRP
- Windows 7 does include SRP Snap-in for backwards compatibility
- Any GPO configuring AppLocker will override a GPO configuring SRP
APPLocker is much more granular than SRPs.
AppLocker allows you enforce the rules and audit them.
AppLocker has a GUI.
Configure UAC
What is UAC?
Windows Vista and UAC changed everything when it came to running programs with administrative rights. Running as a standard user is now the default state for user's programs, even when run by a member of the Administrators group.UAC provides a way for a user to perform administrative tasks without switching users. Standard users are described as accounts "running with least privilege", which makes the session more secure. UAC enables all users to run as standard users and when a task requires administrative credentials, such as for system modifications like when a program is installed, UAC prompts for permission.
Prior to Vista, users frustrated with having to log off and log back on as a Administrator in order to do a log of common tasks, just logged on as an Administrator on a regular basis. Staying logged on as an Administrator leaves the system wide open for malware attacks, not to mention accidental changes to the system that could cause computer problems.
However, Vista's UAC prompting proved to be extremely annoying and many people disabled UAC, all together.
When UAC is disabled, Windows reverts to a mode similar to that of Windows XP. In that case, the LSA does not create filtered tokens, and programs run by members of the Administrators group always run with administrative rights. Further, elevation prompts do not display, but Runas.exe can be used to start a program with administrative rights. Note that disabling UAC also disables Internet Explorer's Protected Mode, so Internet Explorer runs with the full rights of the logged-on user. Disabling UAC also turns off its file and registry virtualization, a feature that enables many a applications that required administrative rights on Windows XP to work with standard user rights.
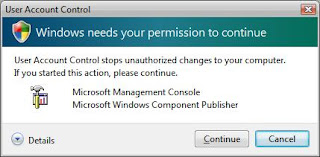
Windows 7 includes changes to UAC that include less prompting for administrative credentials because UAC redefines what a standard user is permitted to do. Windows 7 lets you adjust how often UAC notifies you when changes are made to your computer.
Windows 7 issues two access tokens when authenticating a member of the Administrator's group:
- Full administrator token: used only then administrative privileges are required.
- Standard user token: Used for all actions not requiring administrative privileges.
- Low integrity: A tasks or application that is less likely to compromise the operating system (such as a web browser, email, or word processing programs).
- High integrity: A tasks that has a higher potential for compromising the system.
Default UAC settings allow a standard user to do the following tasks without receiving a UAC prompt:
- Install Windows Updates
- Install drivers from Windows Update or drivers included with the operating system
- View Windows settings (A standard user will be prompted for elevated privileges if changing Windows settings)
- Pair Bluetooth devices with the computer
- Reset network adapter and other network diagnostic and repair tasks
- Read/Write/Execute permissions to all resources
- All Windows privileges
Demo – Configuring Group Policy
Group Policy settings are applied in this order:
- Local
- Local group policy is applied at boot, and again at regular intervals should there be any updates to the policy. You can enforce updates to group policy at any time with the gpupdate /enforce option
- Site
- Domain
- OU
- Start/ type: gpedit.msc in the Search field and press Enter
- Navigate to Computer Configuration/Windows Settings/Security Settings/Local Policies/Security Options
- Scroll to find User Account Control: Behavior of the elevation prompt for standard users and double-click.
- In the dialog box, click Automatically deny elevation request
- Click OK
- Close Local Group Policy Editor
Demo Configuring Notification Settings
Prompt
|
Description
|
Never notify
|
UAC is off
|
Notify me only when programs try to make changes to my computer (do not dim my desktop)
|
When a program makes a change, a prompt appears, but the desktop is not dimmed. Otherwise, the user is not prompted.
|
(Default) Notify me only when programs try to make changes to my computer
|
When a program makes a change, a prompt appears, and the desktop is dimmed to provide a visual cue that installation is being attempted. Otherwise, the user is not prompted.
|
Always notify me
|
The user is always prompted when changes are made to the computer.
|
What is a Firewall?
Windows Firewall is a built-in, host-based, stateful firewall that is included in Windows Vista, Windows Server 2008, Windows XP with Service Pack 2 and later, and Windows Server 2003 with Service Pack 1 and later. Windows Firewall drops incoming traffic that does not correspond to either traffic sent in response to a request of the computer (solicited traffic) or unsolicited traffic that has been specified as allowed (excepted traffic). Windows Firewall helps provide protection from malicious users and programs that rely on unsolicited incoming traffic to attack computers. In Windows Vista and Windows Server 2008, Windows Firewall can also drop outgoing traffic and is configured using the Windows Firewall with Advanced Security snap-in, which integrates rules for both firewall behavior and traffic protection with Internet Protocol security (IPsec).There are two main types of firewalls:
- Network firewalls are located on the network's perimeter.
- Either hardware-based, software-based, or a combination of the two that provide services, including the following:
- Management and control of network traffic by performing dynamic packet filtering (stateful inspection), connection monitoring, and application-level filtering
- Stateful connection analysis by inspecting the state of all communications between hosts and storing connection data in state tables.
- Virtual private network (VPN) gateway functionality by providing IPSec authentication and encryption with Network Address Translation-Traversal (NAT-T) that allows the permitted IPSec traffic to traverse the firewall with public to private IPv4 address translation.
- Host-based firewalls are located on individual hosts within the network.
- In addition to network-based firewalls, host-based firewalls running on the individual computers are needed to provide additional security because network-based firewalls are not enough to provide the protection needed inside the network. Windows Firewall with Advanced Security provides an extra layer of security in your network.
Windows Firewall
Configuring Basic Firewall Settings
The first time a user connects to a network, the user must select a network location. Selecting a network location, automatically sets the appropriate firewall and security settings for that particular network type to ensure the computer is always set to an appropriate security level. The three network locations are:
- Home or work (private) networks. Networks at home or work, trusted networks. Network Discovery is turned on.
- Domain networks. Networks at work that are attached to a domain. Automatically used for a network that has communication with a domain controller. Network Discovery is on by default.
- Public networks. Networks in public places. This location keeps the computer from being visible in public places. Network Discovery is turned off.
When you add a program to the list of allowed programs in a firewall, or when you open a firewall port, you allow a particular program to send information to or from your computer through the firewall. Allowing a program to communicate through a firewall (sometimes called unblocking) is like punching a hole in the firewall.
Each time you open a port or allow a program to communicate through a firewall, your computer becomes a bit less secure. The more allowed programs or open ports your firewall has, the more opportunities there are for hackers or malicious software to use one of those openings to spread a worm, access your files, or use your computer to spread malicious software to others.
It's generally safer to add a program to the list of allowed programs than to open a port. If you open a port, it stays open until you close it, whether or not a program is using it. If you add a program to the list of allowed programs, the "hole" is open only when needed for a particular communication.
- The Properties page is used to configure firewall properties for:
- Domain
- Private network profiles
- Public network profiles
- IPSec settings
- Inbound rules
- Allow or block traffic that matches criteria in the rules
- When Windows is first installed, all unsolicited inbound traffic is blocked. To allow a certain type of unsolicited inbound traffic, you must create an inbound rule to describe the traffic.
- Outbound rules
- Allow or deny traffic originating from the computer that matches the criteria in the rule going out
- Windows Firewall allows all outbound traffic unless a rule blocks it.
- Connection security rules
- Secure traffic by using IPSec while it crosses the network
- Connect rules will often become a ByPass rule. IPSec is most often a ByPass rule. This means it is evaluated and used instead of any inbound or outbound rules.
- Use Connection Security rules to specify that connections between two computers must be authenticated or encrypted. These rules specify how and when authentication occurs, but they do not allow connections.
- Connection security rule types:
- Isolation rules
- Authentication exemption rules
- Server-to-server rules
- Tunnel rules
- Custom rules
- The monitoring interface displays info about:
- Firewall rules
- Connection security rules
- SAs (Security Associations)
Note: You can have more that one profile active at a time.
Traditional firewalls look at layer 3 and 4. They look at source address, destination address, protocol number, protocol ports if needed. Some look at TCP sequence numbers and acknowledgement numbers and flag settings and might do a little more granular work. Some times you have a remote desktop connection, and you have an incoming connection and your machine starts what looks like a new outbound session to give them that remote desktop. To a firewall that looks like a separate type of event because it is using different ports, and such. It is tough to configure.
Now we can make our rules based on programs and that makes it easy when you don’t know all of the TCP, UDP, or port based settings. You can also deal with server or domain isolation to determine if you are communicating with someone on the inside or the outside of your network. You can deal with certificate authentication, a computer can come in as long as they can identify who they are.
Well-Known Ports Used by Applications
- Ports are assigned numbers by IANA
- The numbers are between 0 and 65,535
- Well-know ports range from 0 – 1023
Your source port is only important so that when you reply to me, I know which communication I sent out that you are replying to. If I go to multiple web pages, I will have multiple source ports. As I get all these replies coming in, the source port I sent to you becomes the destination port of the reply coming back.
When an application wants to start communication with an application on a remote host, it creates a TCP or UDP socket. The TCP or UDP socket is a combination of transport protocol, IP address, and a port.
Ports are used in TCP or UDP communications to name the ends of logical connections that transfer data.
PORT
|
Protocol
|
Application
|
80
|
TCP
|
HTTP used by a Web Server
|
443
|
TCP
|
HTTPS for secured Web Server
|
110
|
TCP
|
Post Office Protocol version 4 (POP3) used for email retrieval from email clients
|
25
|
TCP
|
Simple Mail Transfer Protocol (SMTP) that email servers and clients use to send email
|
53
|
UDP
|
Domain Name System (DNS)
|
53
|
TCP
|
DBS
|
21
|
TCP
|
File Transfer Protocol (FTP
|
- Start/Control Panel/System and Security/Windows Firewall/Advanced Settings
- Click on Inbound Rules (you have inbound rules depending what type of network you set up:
- public
- private
- domain
- Go to the right panel and click on New Rule
- What type of rule would you like to create?
- Program
- Port
- Predefined (this is already set up my Microsoft – we will choose Remote Scheduled Tasks Management (RPC))
- Custom
- Click on Next
- You will see some rules displayed. We will choose all of them.
- Click on Next
- Select Block the connection
- Click Finish
- Click Outbound Rules in the left pane
- Go to the right panel and click on New Rule
- Click on Port
- Click on Next
- Does this rule apply to TCP or UDP?
- TCP
- UDP
- Choose TCP
- Under Does this rule apply to all remote ports or specific remote ports?,
- All remote ports
- Specific remote ports:
- Enter 80 in the text box beside Specific remote ports:
- Click on Next
- Block the connection is selected
- Click on Next
- When does this rule apply?
- Domain
- Private
- Public
- Click on Next
- Specify the name and description of this rule. Enter Block the Internet into the Name: text box
- Click on Finish
- Go to your Start button and enter http://www.bing.com
- You will see the web page is now blocked
- You can now right-click the rule in Windows Firewall with Advanced Security to delete the rule
Compatibility Features in Internet Explorer 8
Allows you to click on the compatibility button to make sure you can see a web page in the browser version it was designed for.
- Web sites display in IE8 Standards Mode by default.
- The Compatibility View button can be used to fix sites that render differently than you expect.
- IE8 remembers the websites that have been rendered in Compatibility View.
- The button needs only to be pressed once for a particular site, unless it is removed from the list.
- IE8 ships with a list of sites that are known by Microsoft to require Compatibility View.
- The list is updated through Windows Update or Automatic Updates on a regular basis.
- Internal websites created for IE7 will work.
- Intranet websites display in IE7 Standards mode by default.
- Group Policy can be used to set a list of websites that should be rendered in Compatibility View.
- You can switch in and out of Compatibility View without requiring a restart of the browser.
- There is a new entry on the Tools menu that allows for advanced configuration of the Compatibility View.
- The Application Compatibility View Toolkit (ACT) helps IT professionals to resolve compatibility problems with IE8 and internal applications.
- The Internet Explorer Compatibility Evaluator within ACT helps IT professionals determine potential compatibility problems with websites.
- When ACT runs, a log is created showing compatibility issues along with an error message and a link to a white paper describing mitigation and fixes.
Enhanced Privacy Features in Internet Explorer 8
- InPrivate browsing
- While you are browsing the Internet, there will be no logs, no cookies stored, no temporary files. All of the tracking will be gone when you are done to help protect data and privacy.
- InPrivate filtering
- Monitor the frequency of third-party content as it appears across your websites
- An alert or frequency level can be configured (initially set to three) and third-party content is blocked when the frequency level is reached.
- One web page could have 15 sessions all by itself because of linking to third-party sites
- Enhance delete browing history
- You can selectively delete your browsing history
- Group Policy or the Internet Explorer Administration Kit has Delete Browsing History options that can be configured by Administrators. note: Favorites can also be configured automatically.
SmartScreen Feature in Internet Explorer 8
- The SmartScreen Filter in IE8 builds on the Phishing Filter technology introduced in IE7
- The SmartScreen Filter relies on a Web service backed by a Microsoft-hosted URL reputation database. Microsoft keeps track of sites with malicious content.
- If the Web site is known to be unsafe, it is blocked and the user is notified
- Per-user ActiveX
- Standard users can install ActiveX controls that are sometimes needed while browsing without requiring admin privileges
- Use Group Policy to preset allowed controls and related domains
- XSS Filter
- IE contains a filter that helps to protect against XSS attacks.
- Identifies and neutralizes a cross-site scripting (XXS) attack if it is replayed in the server’s response. XXS installs malicious code on your website.
- DEP/NX protection
- Prevents code from running in memory that is marked non-executable (NX)
- Makes it harder for attackers to exploit buffer overruns
- Applies to Internet Explorer and the add-ons it loads
- Enabled by default in IE8
- Open Internet Explorer
- Select Tools in the Menu Bar
- Select Compatibility View Settings
- Add websites you have problem viewing that maybe were designed for earlier versions on the browser
- Select Internet Options
- Select Browsing history and click Delete
- On the Delete Browsing History dialog box is:
- Preserve Favorites website data
- Temporary Internet files
- Cookies
- History
- Form data
- Passwords
- InPrivate Filtering data
- Select Delete to delete the browing history
- Select the Security tab
- You have the ability to change the default settings for the different types of zones, but it is probably better to leave them the way they are set. Medium-high is the best choice.
- Click OK
- Click on Tools
- Select InPrivate Browsing
- It gives you a tutorial on InPrivate Browsing. You will see InPrivate in the URL bar. You won’t see the history. This is good for working in a public place.
Configure Windows Defender
What is Malicious Software?
Malicious software is software designed to deliberately cause harm to a computer.
- Types:
- Viruses
- Worms
- Spyware
- Adware
- Trojan horses
- What Malicious Software can do:
- Poor performance
- Loss of data
- Compromise of private info
- Reduction in end user efficiency
- Unapproved computer configuration changes
What is Windows Defender?
Windows Defender needs to have updates to recognize new malware and update its signatures.
Windows Defender does not slow your system like other third-party solutions. You can configure it to your liking. For example, it doesn’t have to scan all web pages before presenting it to you. Or, scan all email before it shows up in your inbox. You have the flexibility to alter they way you are monitored. You have the ability to do real-time protection and look at files you are downloading and running.
Note: Even though your malware detection software might be behind by a few hours or days, if you are also using APPLocker, Windows Firewall, User Access Control (UAC), this gives you the recommended in-depth security that is recommended.
Demo – Configure Windows Defender
- Start/Type: Windows Defender in the Search bar
- Click on Tools
- Click on Options
- Under Frequency:, click on Monday 5:00 AM
- Under Type:, select Quick Scan
- Check the Check for updated definitions before scanning text box and Run a scan only when system is idle text box
- In the left panel, click on Default actions
- Under Severe alert items:, select Remove
- Under High alert items:, select Remove
- Under Medium alert items:, select Quarantine
- Under Low alert items:, select Recommended action based on definitions
- In the left panel, click on Real-time protection
- Leave the following boxes checked:
- Use real-time protection (recommended)
- Scan downloaded files and attachments
- Scan programs that run on my computer
- In the left panel, click on Excluded files and folders, click Add to exclude particular files you do not want scanned
- In the left panel, click on Exclude file types, , click Add to exclude particular files types you do not want scanned
- In the left panel, click on Advanced
- Scan archive files
- Scan e-mail
- Scan removable drives
- Use heuristics
- Create restore point
- In the left panel, click on Administrator
- Use this program
- When the setting is on, this program will alert all users if spyware or other potentially unwanted software attempts to run or install itself on this computer.
- Display items from all users of this computer
- When the setting is on, this program will allow you to see the History, Allowed items, and Quarantined items from all users. Items are hidden by default to protect user privacy.
- Click Save
 |
| London |












No comments:
Post a Comment
"Comment As:" anonymous if you would rather not sign into an account!